SQL Password Bypasser
SQL Password Bypasser by Thegrideon Software is an advanced tool for MS SQL Server password replacement and recovery. It allows you to instantly reset or change any SQL Server account password or start password recovery search with a very flexible search range setup. SQL Password Bypasser works with all versions including the latest MS SQL Server 2022. You may also check SQL Server Forensics tool for in-depth analysis.
SQL Password Bypasser Features:
- Works with all modern versions: MS SQL Server 2000 - 2022.
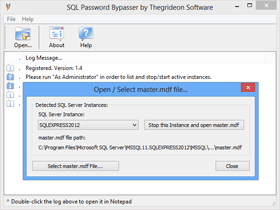
- Lists SQL Server instances with associated master.mdf files.
- Allows you to Start / Stop SQL Server to edit master.mdf.
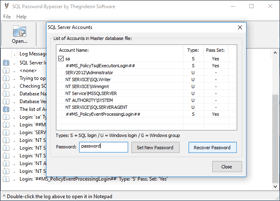
- SQL Server Account Password can be cleared or changed instantly.

- Several password search attacks can be configured and queued:

- advanced mixed attacks for precise search range setup:
- multi-position moves to cover modern password policies;
- simple modifications: add part(s) copy, replace chars, etc.
- typing errors, case switching, char substitutions;
- brute-force attacks based on a charset and length selected:
- limit number of equal, capital or special chars or digits;
- dictionary attacks with modifications (several wordlists are included):
- advanced keyboard layouts-aware recovery technique;
- password in reverse, capitalized, uppercased, lowercased;
- highly optimized code (SSE, AVX, AVX2) guarantees maximum performance;
- audio, script or web address based post-search notification;
- x32 and x64 editions are supported.
- Windows 7 - Windows 11.
MS SQL Server Logins and Passwords (as well as database configurations) are stored in SQL Master Database file named "master.mdf". Passwords are stored hashed, so they are hard to recover, but passwords can be replaced instantly. SQL Password Bypasser allows you to stop active SQL database, list logins, reset (change) selected account password and start the database. Account password might be useful outside of the SQL Server environment, therefore password search is also an option. SQL Password Bypasser allows you to set several attacks in a queue: dictionary, brute-force or mixed (combination of dictionary, sequential and fixed parts). You can set almost any search pattern from independent parts with virtually endless number of combinations. Search speed is millions of passwords per second.
Trial version allows you to check compatibility. It lists accounts in "master.mdf". Password recovery test runs are 15 min limited.
All trademarks are the property of their respective holders.